ABSTRACT
The leading method of correspondence is clearly through voice trade. There are essentially two different ways through which voice can be effortlessly communicated on an organization: PSTN (Public Switched Telephone Network) and VoIP (Voice over Int…
See full abstracts, authors, references, citations & other publication information.
+
…ernet Protocol).
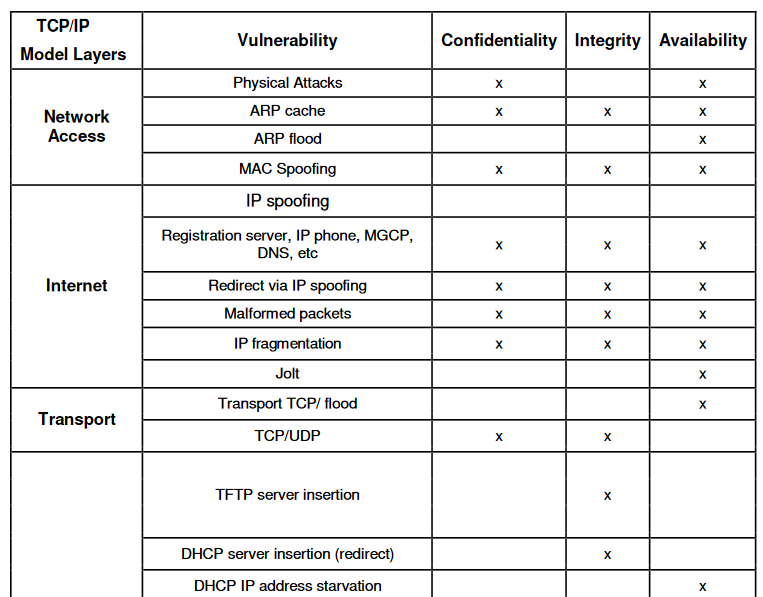
Mainly represented by SIP, VoIP protocols and implementations contain several vulnerabilities,
particularly related to their complexities and in the face of interoperability of telephony
equipment’s.
It was by identifying a lack of literature with focus in security and potential vulnerabilities of the
SIP Protocol that we propose in this document. We attempt to provide a theoretical analysis from
security aspects used by one of the signaling call protocols, Session Initiation Protocol (SIP).
It is intended to lucidly illustrate and identify threats, vulnerabilities, security mechanisms,
developed methods and protocols and, finally over time improvements.
Full Text/Reference Website: https://www.cscjournals.org/library/manuscriptinfo.php?mc=IJCSS-1637
AUTHORS
Mr. Bruno Cruz – Department of Informatics Engineering, Coimbra University, Coimbra – Portugal
Mr. Rui Filipe Pereira – Lab UbiNET – Computer Science, Security and Cybercrime, Polytechnic Institute of Beja, Beja, – Portugal
KEYWORDS
Session Initiation Protocol (SIP), SIP Security, Voice over IP (VoIP).
Indexing Keywords: Session Initiation Protocol: Security Issues Overview, Session Initiation Protocol, Security Issues Overview, Security Issues Overview: Session Initiation Protocol.
Pages: 181-192
Revised: 31-10-2021
Published: 01-12-2021Published in International Journal of Computer Science and Security (IJCSS).
Volume: 15
Issue: 6
Publication Date: 01-12-2021
*Randomly selected references used in the publication “Session Initiation Protocol: Security Issues Overview”.
- A. D. Keromytis, “Voice-over-IP Security: Research and Practice,” in IEEE Security & Privacy, vol. 8, no. 2, pp. 76-78, March-April 2010, doi: 10.1109/MSP.2010.87.
- I. M. Tas, B. G. Unsalver and S. Baktir, “A Novel SIP Based Distributed Reflection Denial-of-Service Attack and an Effective Defense Mechanism,” in IEEE Access, vol. 8, pp. 112574-112584, 2020, doi: 10.1109/ACCESS.2020.3001688.
- Lazzez, A. (2013). VoIP Technology: Security Issues Analysis. ArXiv, abs/1312.2225.
- McGann, S. (2005). An Analysis of Security Threats and Tools in SIP-Based VoIP Systems.
- P. Biondi, S. Bognanni and G. Bella, “VoIP Can Still Be Exploited – Badly,” 2020 Fifth International Conference on Fog and Mobile Edge Computing (FMEC), 2020, pp. 237-243, doi: 10.1109/FMEC49853.2020.9144875.
- Pereira D., Oliveira R. (2021) Detection of Signaling Vulnerabilities in Session Initiation Protocol. In: Camarinha-Matos L.M., Ferreira P., Brito G. (eds) Technological Innovation for Applied AI Systems. DoCEIS 2021. IFIP Advances in Information and Communication Technology, vol 626. Springer, Cham. https://doi.org/10.1007/978-3-030-78288-7_20
- P. Segec, M. Moravcik, J. Hrabovsky, J. Papán and J. Uramová, “Securing SIP infrastructures with PKI — The analysis,” 2017 15th International Conference on Emerging eLearning Technologies and Applications (ICETA), 2017, pp. 1-8, doi: 10.1109/ICETA.2017.8102525.
- Ramsdell, B. C. (1999, Junie). S/MIME Version 3 Message Specification. doi:10.17487/RFC2633
- Rescorla, E. (2018, Augustus). The Transport Layer Security (TLS) Protocol Version 1.3. doi:10.17487/RFC8446
- R. Farley and X. Wang, “VoIP Shield: A transparent protection of deployed VoIP systems from SIP-based exploits,” 2012 IEEE Network Operations and Management Symposium, 2012, pp. 486-489, doi: 10.1109/NOMS.2012.6211937.
CITATIONS
Citations used in the publication “Session Initiation Protocol: Security Issues Overview”.
Currently there are no citations collected for this publication at scholarlyabstracts.com.
-
CONTACT US
Please feel free to us at scholarlyabstracts@gmail.com if you wish to:
- Get your journal, conference or thesis, registered with us.
- Update this publication content.
