ABSTRACT
As the increase of adopting database systems as the key data management technology by organizations for day-to-day operations and decision making, the security and privacy issues of these systems becomes crucial. Achieving privacy-preserving range …
See full abstracts, authors, references, citations & other publication information.
+
…query efficiently is a difficult
challenge in practice. Many privacy-preserving protocols use secure multi-party computation
(MPC) as building block, which present elegant privacy and security, but brings too much
computation and communication overheads at the same time.
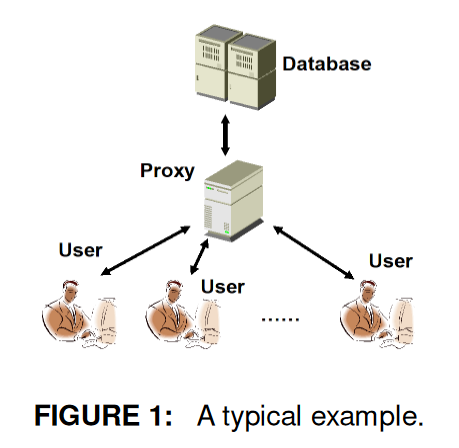
In this paper, we consider the three-party database system model: A client performing
privacy-preserving range queries through a Proxy (trusted third party, TTP), to a Server’s database.
The User does not learn how the query applied on the database, nor any other quarriable attributes
that the database may contain. The Proxy does not learn any information about the Server’s private
data, though he interacts with the Server directly. The Server on the other hand, learns nothing
about the User’s query.
We propose two practical privacy-preserving query schemes for database system. The basic idea
of our schemes is to first convert each data entry into a set of concrete numbers, which is called
attribute value numericalization. Then combines in a novel way several efficient cryptographic
techniques, such as secure hash function, pseudo-random function, XOR, etc. to check whether
the records match a query. The experimental evaluation (using the data sets collected by UCI KDD)
of our prototype implementation show that our protocols incur reasonable computation and
communicating overhead for added privacy-preserving benefit and perform better than those
MPC-based solutions.
Full Text/Reference Website: https://www.cscjournals.org/library/manuscriptinfo.php?mc=IJCSS-1680
AUTHORS
Mr. Miaomiao Zhang – Computer Science Department, Manhattan College, Riverdale NY, 10583 – United States of America
KEYWORDS
Privacy-preserving, Database, Hidden Queries, Hash, Efficiency.
Indexing Keywords: Privacy-Preserving Database System with Hidden Queries, Privacy-Preserving Database System, Privacy-Preserving Hidden Queries, Privacy-Preserving Database Hidden Queries.
Pages: 43-58
Revised: 30-09-2022
Published: 31-10-2022Published in International Journal of Computer Science and Security (IJCSS).
Volume: 16
Issue: 4
Publication Date: 31-10-2022
*Randomly selected references used in the publication “Privacy-Preserving Database System with Hidden Queries”.
- Agrawal, R., Evfimievski, A. and Srikant, R. (2003). Information sharing across private databases. International Conference on Management of Data, 132-143.
- Hayata, J. & Schuldt, J. & Hanaoka, G. & Matsuura, K. (2020). On Private Information Retrieval Supporting Range Queries. Computer Security – ESORICS 2020, 25th European Symposium on Research in Computer Security, Proceedings, Part II, pages 674-694.
- Hayata, J., Schuldt, J.C.N., Hanaoka, G., Matsuura, K. (2020). On Private Information Retrieval Supporting Range Queries. In: Chen, L., Li, N., Liang, K., Schneider, S. (eds) Computer Security – ESORICS 2020. ESORICS 2020. Lecture Notes in Computer Science(), vol 12309. Springer.
- Huberman, B. A., Franklin, M. and Hogg, T. (1999). Enhancing privacy and trust in electronic communities. In ACM Conference on Electronic Commerce, pages 78-86.
- Kushilevitz, E. and Ostrovsky, R. (1997). Replication is NOT needed: SINGLE database, computationally- private information retrieval. In IEEE 38th Annual Symposium on Foundations of Computer Science, pages 364-373.
- Liang, G. and Chawathe, S. S. (2004). Privacy-preserving inter-database operations. In Intelligence and Security Informatics, volume 3073, pages 66-82. Springer Berlin/Heidelberg.
- Beimel, A. and Stahl, Y. (2007). Robust Information Theoretic Private Information Retrieval. J. Cryptol., 20(3):295-321.
- Neuman, B. C. and Tso, T. (1994). Kerberos: an authentication service for computer networks. Communications Magazine, IEEE, 32:33-38.
- Reiter, M. K., Franklin, M. K., Lacy, J. B. and Wright, R. N. (1996). The omega key management service. In ACM Conference on Computer and Communications Security, pages 38-47.
- Tillem, G., Candan, O.M., Sava ̧s, E., Kaya, K. (2016). Hiding access patterns in range queries using private information retrieval and ORAM. In: Clark, J., Meiklejohn, S., Ryan, P.Y.A., Wallach, D., Brenner, M., Rohloff, K. (eds.) FC 2016. LNCS, vol. 9604, pp. 253-270. Springer, Heidelberg.
CITATIONS
Citations used in the publication “Privacy-Preserving Database System with Hidden Queries”.
Currently there are no citations collected for this publication at scholarlyabstracts.com.
-
CONTACT US
Please feel free to us at scholarlyabstracts@gmail.com if you wish to:
- Get your journal, conference or thesis, registered with us.
- Update this publication content.
